The main purpose of a firewall is to inspect data packets moving in and out of a network, allowing legitimate packets to pass through and blocking any malicious traffic. Once in place, a firewall can be used to create a secure network, by separating internal sources of data traffic, external sources of data traffic, and even applications in some cases.
To ensure that only the right data gets delivered to the intended recipient in a safe manner, firewalls normally use a predetermined set of rules to assess each data packet.
There are many different types of firewalls, each designed to secure networks, albeit in slightly different ways.
Table of Contents
Types of Firewalls
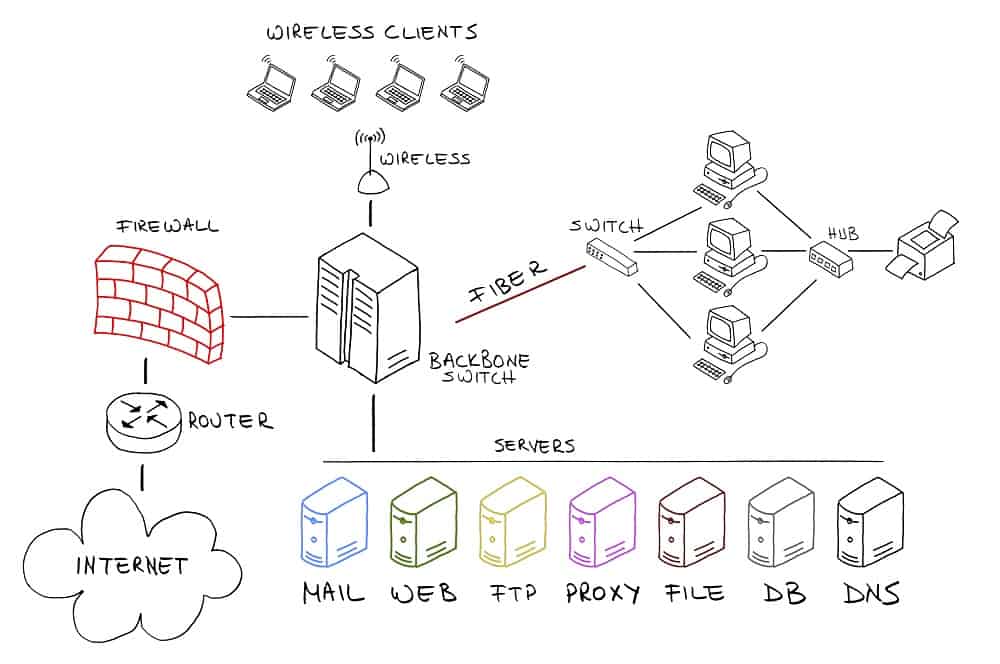
Packet-Filtering Firewall
Installed in-line at a switch or router, Packet-filtering firewalls are designed to act as a traffic checkpoint for all data packets entering or leaving a network. Bearing the oldest and most basic architecture, these firewalls do not route data packets. They perform a surface level inspection of the data packets, checking things such as the port number, packet type, IP address of origin and destination among others.
Packet-filtering firewalls drop data packets that fail the inspection – which means that the data ceases to exist and is not transmitted.
This type of firewall has a number of advantages; they tend to be more affordable and cost efficient with a single device being capable of securing an entire network. Furthermore, since they are very efficient and fast when it comes to scanning data traffic, these firewalls have little or no effect on the user experience, network performance and other resources.
However, given the fact that they only offer surface inspection capabilities, packet-filtering firewalls are not as secure as other types.
Circuit-Level Gateway
Circuit-level gateways are designed to monitor network traffic, and identify threats, without consuming a significant level of resources. Deployed between the local and remote hosts, these firewalls are designed to monitor data traffic by establishing whether each packet is coming from a legitimate session. To do this, circuit-level firewalls seek to verify the TCP (Transmission Control Protocol) and monitor other network protocol initiation messages.
These firewalls normally reject any and all data traffic that has not been requested.
Circuit-level gateway firewalls do not consume a lot of resources; and are considered to provide a higher level of security in comparison to packet-filtering firewalls.
However, these firewalls do not inspect the data packet itself; thus offering no application layer monitoring. To keep any data packets that have the right TCP handshake but also contain malware inside, circuit-level gateways must be used with other types of firewalls.
Stateful Firewall
Stateful firewalls are designed to provide more protection than both packet-filtering and circuit-level gateways. They combine both packet filtering and TCP verification capabilities in one convenient package.
All of the data flowing through the firewall is monitored and filtered in accordance to a set of dynamically created rules. To create these rules, the firewall notes all the important connection information in a state table/database whenever a connection is established and data is requested.
Stateful firewalls provide a more thorough level of security. Furthermore, these firewalls give users/administrators a higher level of control over what is allowed to leave or enter their network.
On the other hand, stateful firewalls tend to consume a more resources; and can therefore slow the transmission of legitimate data packets.
Stateless Firewall
Designed to be faster at monitoring data traffic than their stateful counterparts, stateless firewalls consider fewer details when inspecting network traffic. These firewalls are designed to inspect traffic, and identify threats by checking static information, such as source and destination addresses, of individual data packets; before following a set of preapproved conditions to guide allowed packets into the network.
By inspecting data packets individually, these firewalls do not consider the full context of each network connection.
Since stateless firewalls are faster than their stateful counterparts, they are suited to applications characterized by high network traffic. However, since they don’t consider the entire pattern in which packets are being transmitted in, assessing each one individually, they are susceptible to threats spread out in a number of packets.
Application-Level Gateway
Designed to act as the only point of entry or exit to and from a network, an application-level gateway is technically considered to be a proxy, and may be referred to as a proxy firewall as well. These firewalls can be deployed in the form of a device or through cloud applications.
To secure a network, these firewalls act like a proxy – thus, breaking any direct connection to the network – establishing a connection with the source of traffic and then inspecting the incoming data packets. The inspection includes checking the TCP handshake as well as the packet itself; just like a stateful firewall would. Some application-level gateways also perform a deep inspection of the packets, by checking the contents therein.
After inspection, approved data packets are then sent/connected to their destination.
One of the main advantages of these firewalls is the extra layer of security and anonymity afforded to protected networks; through the creation of an additional layer of separation between the sources of data packets (outside the network) and their destinations (within the network).
On the flip side, these firewalls create a significant lag in the transfer of data packets by introducing an additional step in the process.
Next-Generation Firewall
While there is no generally accepted definition of Next-generation firewalls, these firewalls are essentially designed to offer multifunctional capability.
As the most recent additions to the firewall product market, typical next-generation firewalls combine a number of data packet inspection technologies and methods, including surface inspection, TCP handshake verification, malware filtering, DPI (Deep Packet Inspection) and IPSs (Intrusion Prevention Systems), in one package to provide the most comprehensive level of security to networks.
To provide the most accurate data packet inspection insights, these firewalls monitor all traffic from Layer 2 to the application layer.
Even with their multifunctional capability, these firewalls need to be deployed in conjunction with other security systems, to maximize functionality.