Firewalls are present in both corporate and consumer settings. Many devices even come with built-in firewalls (Mac, Windows, and Linux). A firewall, regardless of the type being implemented is an essential part of network security.
Firewalls are categorized based on how they work to filter data or by the system they protect. The types of firewalls are as follows (listed ascendingly based on packet context): packet-filtering firewall, stateful inspection firewall, proxy firewall (application-level gateway), and next-generation firewall (NGFW).
Table of Contents
What is a Firewall?
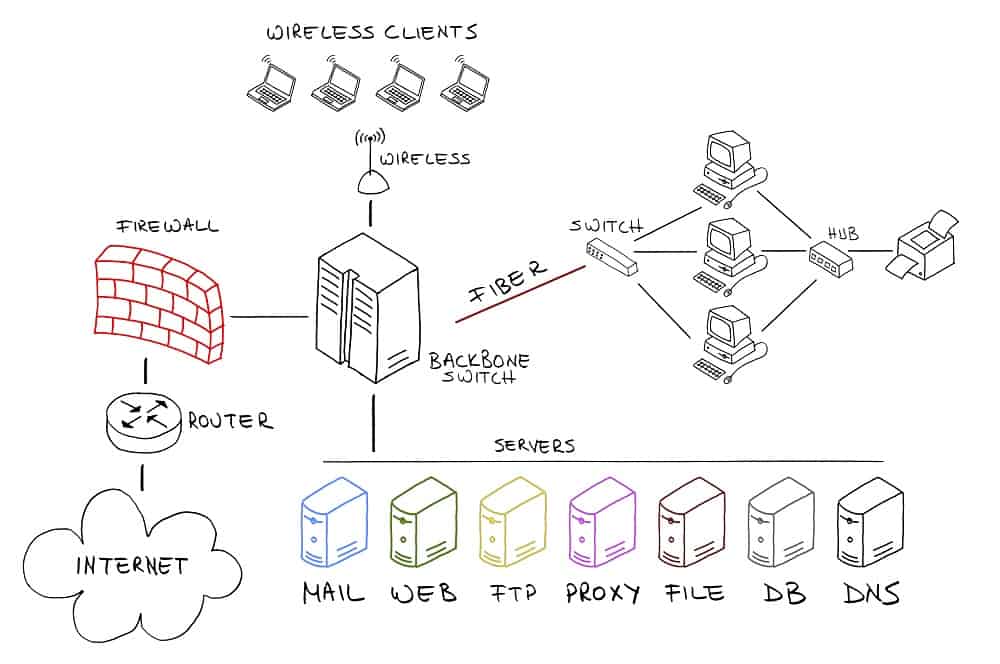
A firewall is firmware or software that prevents unauthorized access to a network. A firewall works inline across a network and inspects both incoming and outgoing network traffic. The firewall will either permit or block packets based on pre-configured security rules.
The overarching goal of a firewall is to create a barrier between your internal network and the incoming traffic from external sources (the internet).
Forms of Firewall
Firewall can come in different forms, namely: software, hardware, and cloud-based.
Software Firewall
A firewall installed on a computer is called a software firewall. The software firewall regulates traffic through the port numbers as well as the applications.
Hardware (Appliance) Firewall
A hardware firewall is physical device, similar to a server, that filters traffic going to a computer. Hardware firewalls are situated between internal and external networks (the internet).
Hardware firewalls use their own hardware, software, and networking components. These firewalls allow for granular control over traffic and serve as a gateway.
Cloud-based Firewall
A cloud-based firewall can be installed in a network either as a standalone application or as a Software-as-a-Service (SaaS). SaaS firewall is a firewall service that is rendered through the internet rather than as an application on the computer.
Types of Firewall
The various types of firewall can be categorized based on their structure and method of operation.
Packet-Filtering Firewall
Packet-filtering is the oldest and most basic type of firewall. They are inserted at junction points between devices like routers and switches. These firewalls do not route packets, they simply compare them to pre-defined criteria.
They perform basic checks based on the data packet information such as origin and destination IP address, port number, packet type, and other surface-level information. A packet that doesn’t match the criteria is dropped and not forwarded.
As a stateless firewall (inspection of the protocol header), there is not a deep inspection of the contents of each packet. As a result, there is not a degradation in system performance.
Circuit-Level Gateway
Circuit-level gateways are similar to the packet-filtering firewall. A circuit-level gateway checks the validity of packets at the session layer of the OSI model – Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) – and functions as a relay by handing off incoming packets to other hosts.
Like the packet-filtering firewall, the circuit-level gateway only checks basic information like source and destination IP, ports, time of day, protocol, as well as username and passwords. When a connection is permitted, no further checks are performed.
Stateful Firewall
A stateful firewall monitors the full state (context-sensitive) of active network connection. As a connection is started and data is requested, the stateful inspection builds a state table and stores packet information (source and destination IP address, as well as source and destination port).
As this connection information is stored in the state table, the firewall will create rules to allow anticipated traffic.
Application-Level Firewall
An application-level firewall or application gateway is usually a component of a proxy server. The proxy firewall acts as the intermediary between clients and servers on the internet. The proxy firewall monitors incoming traffic like HTTP and FTP protocols.
The proxy firewall uses stateful inspection as well as deep packet inspect (DPI) on incoming traffic. Meaning apart from source and destination IP, and ports, it also has logging capabilities that evaluate the contents of the packet.
To illustrate: A client sends a request to access a web page. The packet is intersected by the proxy server. The proxy then forwards the packet to the web server by pretending to be the client. The web server responds and gives the proxy the information which is sent to the client.
Next-Generation Firewall
Next-generation firewall (NGFW) is a security device that combines a number of the security protocols in other firewall iterations: packet, stateful, and DPI. Meaning, NGFW focuses on the actual payload as apposed to the header information (surface-level).
Granted, there isn’t a specific definition that governs exactly what a “Next-Generation” firewall is. For instance, many include deep packet inspection, TCP handshake checking, as well as surface-level packet inspection. They can also feature intrusion prevention systems (IPSs) , malware filtering, and antivirus.